Identity risks that could leave your organization vulnerable to attack.
Identity risks that can leave every organization vulnerable to attack.
In today’s digital landscape, privileged users are the keys to your organization’s most valuable data and assets. A compromised privileged user account can open the door to all kinds of cyber threats.

Drawing from a year’s worth of identity risk assessments of organizations across multiple industry segments, a study by Proofpoint found exploitable privileged identity risks at a rate of 1 in 6 endpoints.
These risks include:
- Unmanaged local admins with stale passwords
- Misconfigured users with unnecessary privileges
- Cached credentials left exposed on endpoints
Privileged users are powerful.
Many organizations are unaware of these risks and therefore are unable to properly manage them.
Privileged users have the ability to reset passwords, change policies, install software, and extract or encrypt data. If an attacker compromises an endpoint of a privileged user, it is at great risk to the company and its critical data. When exploited, identity risks allow attackers to gain initial access, elevate privileges, evade defenses, and in some cases, take complete control.

Unmanaged Identity Risks
Unmanaged identity risks include:
Outdated local admin passwords
Using temp or test admin accounts
or local admins who have not been enrolled in an account management system.
Default passwords
- 21% of local admins use the default account name (Administrator)
Using default account names such as “Administrator” or “Admin”, for local admin accounts lowers the barrier to entry for attackers. Particularly if these default admin accounts all use the same password.
Outdated passwords
Outdated passwords is also an identity risk. We recommend admin passwords be updated every 30 to 90 days. The older a password becomes, the more susceptible it is to brute-force attacks, particularly in the case of password reuse.
Failure to set password
- 1 in 180 local admin passwords have never been set
Another risk is failing to set a local admin password in the first place. Some may argue in favor of not setting an admin password, however this approach greatly increases the risk of insider attack. And in the case of a lost or stolen device, it could be catastrophic.
Unknown local admins
- 1 in 200 local admins were completely unknown by the organization
Another unmanaged risk is the presence of completely unknown local admins. These admins tend to be named “temp” or “test.” In most cases, organizations these admin account have been forgotten, but these accounts are highly privileged and a big risk.

Misconfigured Identity Risks
Misconfigured identity risks fall under a category we call “shadow admins.” Shadow Admin are accounts in your network that have admin privileges but are often overlooked because they are not members of any Active Directory groups.
The hidden dangers of Shadow Admins
- 40% of shadow admin risks can be exploited in one step
If an attacker compromises one of these misconfigured identities, a single action such as resetting the password of a domain admin would allow the attacker to elevate their privileges in order to have increased access to your businesses data and applications.
- 13% of shadow admins have Domain Admin privileges
Less common but more concerning are shadow admins with the power to take over the entire domain. If attackers compromise a shadow admins, with Domain Admin privileges, they can do just about anything.
How are Shadow admin accounts created?
Users who have been promoted into a new position and their privileges have not be adjusted
Users who were mistakenly added to privileged groups
Users who were temporarily granted permissions and later forgotten
Users who were created in an unusual or unexpected event
Exposed Identity Risks
Exposed risks include privileged identity information left in:
- Cached credentials
- In-app password stores
- OS password stores
- Disconnected or “hanging” remote desktop protocol (RDP) sessions
These are the digital equivalent of leaving your username and password written on a sticky note. Attackers have a variety of tools to exploit these credentials.
Web browsers are one of the main sources of exposed identity risks and when privileged credentials become exposed in web browsers, they often go unnoticed. Cyber attackers have automated collection and exploitation tools to steal these credentials. Within minutes, attacks can infect large swaths of an organization.
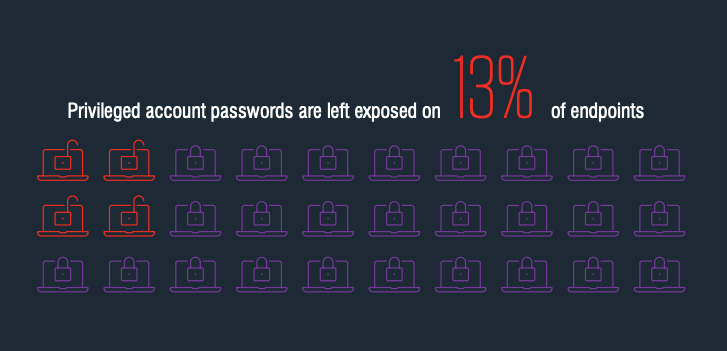
- Privileged account passwords are left exposed on 13%of endpoints.
- More than 1 in 10 endpoints have exposed privileged account passwords.
- 55% of exposed privileged identities are stored in browsers
In conclusion,
The amount of identities organizations must manage has soared in recent years as businesses expand their reliance on growing numbers of digital systems and applications. This makes every organization vulnerable to unmanaged, misconfigured, and exposed identity risks.
Because of this expedited growth, managing and securing identities has grown to feel impossibly complex. In an age where attackers leverage identity as a primary course of attack, even short exposures of privileged identities carry huge risks.
It’s important for organizations to understand the weight of these risks and to place importance on managing their internal identities. Investing in Privileged Access Management and Multi Factor Authentication tools to protect your most privileged accounts is a great place to start, however cleaning up and maintaining outstanding identity risks should also be a focus. Regularly scanning for vulnerable code and applications is just as critical as scanning for vulnerable identities.
It comes down to visibility.
Even the most well-intentioned security teams can’t mitigate identity risks that they can’t see. It can be difficult for organizations to gain visibility into their risk of an identity based attack.
Some organizations have tried to manage their identity risk through red team exercises, annual audits, scripts and spreadsheet, but many of these efforts are fall short. Just as cybersecurity teams manage vulnerabilities through regular scans, these same teams need the ability to scan for vulnerabilities in the identities used to run their business — automatically and continuously.
Learn more about how Partek can provide insight into your vulnerabilities to help you mitigate risks with a people-centric cybersecurity strategy:
Our free cyber security assessment helps identify critical vulnerabilities within your business. These insights are invaluable to create a comprehensive approach to cyber security for your business. It’s quick, simple, and there’s no obligation. Take the assessment using the button below.



