Numbers Hit an All-Time High :
Top Data Breaches of 2023
The battle against cyber threats is an ongoing challenge. Unfortunately, 2023 has proven to be a watershed year for data breaches. Data compromises have surged to an all-time high in the U.S. This is based on data from the first 9 months of the year. Meaning that numbers will only end up higher for the year.
The last data breach record was set in 2021. That year, 1,862 organizations reported data compromises. Through September of 2023, that number was already over 2,100.
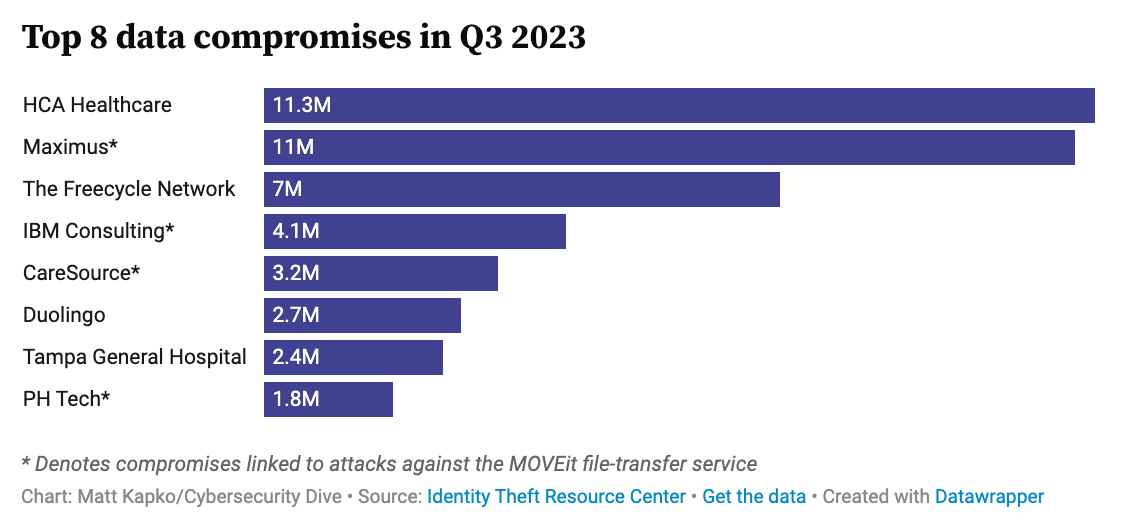
In Q3 of 2023, the top data compromises were:
This data underscores the relentless efforts of cybercriminals to exploit vulnerabilities and access sensitive information. What are the main drivers of this increase?
The Size of the Surge
The numbers are staggering.
Data breaches in 2023 reached unprecedented levels, increasingly significantly compared to previous years. The scale and frequency of these incidents is concerning. They emphasize the evolving sophistication of cyber threats. As well as the challenges organizations face in safeguarding their digital assets.
- The average cost of a data breach was $4.45 million in 2023, the highest average on record.
- The average lifecycle of a breach is 277 days from identification to containment.
- Over 2,100 organizations filed data breach notices through the first nine months of 2023, beating the previous record of 1,862 data compromises in 2021.
- In 2023, 74% of breaches involved a human element.
Healthcare Sector Under Siege
One of the most disturbing trends is the escalating number of breaches in healthcare. Healthcare organizations are the custodians of highly sensitive patient information. As a result, they’ve become prime targets for cybercriminals. The breaches jeopardize patient privacy. They also pose serious risks to the integrity of medical records. This creates a ripple effect that can have long-lasting consequences.
Ransomware Reigns Supreme
Ransomware attacks continue to dominate the cybersecurity landscape. Cybercriminals are not merely after data. They are wielding the threat of encrypting valuable information. Then demanding ransom payments for its release. The sophistication of ransomware attacks has increased. Threat actors are employing advanced tactics to infiltrate networks and encrypt data. They are also using many different methods to extort organizations for financial gain.
Supply Chain Vulnerabilities Exposed
Modern business ecosystems have an interconnected nature. This has made supply chains a focal point for cyberattacks. The compromise of a single entity within the supply chain can have cascading effects. It can impact several organizations downstream. Cybercriminals are exploiting these interdependencies. They use vulnerabilities to gain unauthorized access to a network of interconnected businesses.
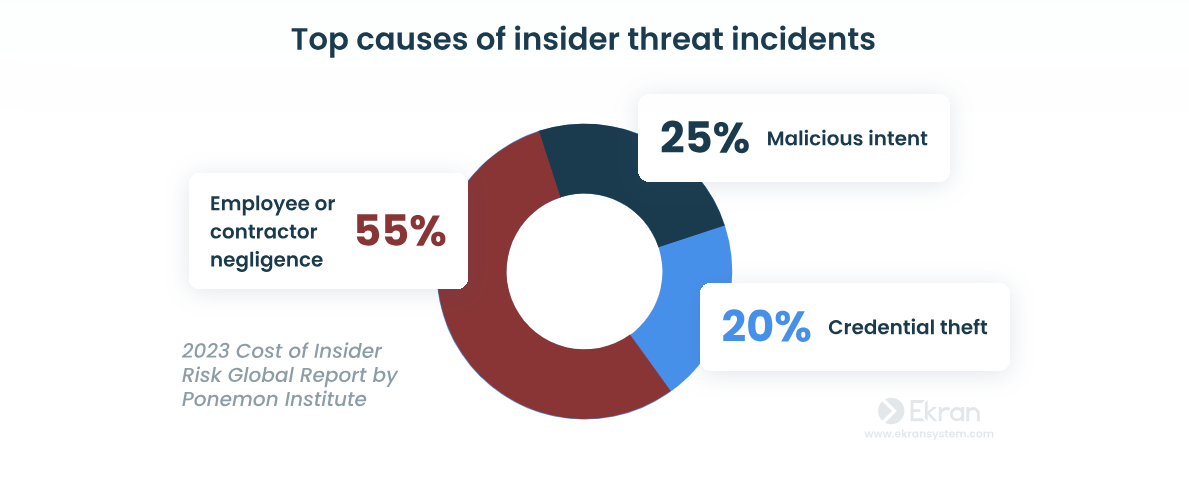
Emergence of Insider Threats
External threats remain a significant concern. But the rise of insider threats is adding a layer of complexity. It’s added to the already complex cybersecurity landscape. Insiders inadvertently contribute to data breaches. Whether through malicious intent or unwitting negligence. Organizations are now grappling with a challenge. They need to distinguish between legitimate user activities and potential insider threats.
IoT Devices as Entry Points
The proliferation of Internet of Things (IoT) devices has expanded the attack surface. There’s been an uptick in data breaches originating from compromised IoT devices. These connected endpoints range from smart home devices to industrial sensors. They are often inadequately secured. This provides cyber criminals with entry points to exploit vulnerabilities within networks.
Critical Infrastructure in the Crosshairs
Critical infrastructure has become a target of choice for cyber attackers. This includes energy grids, water supplies, and transportation systems. The potential consequences of a successful breach in these sectors are often financial. But that’s not all. They can also extend to public safety and national security. As cyber threats evolve, safeguarding critical infrastructure has become an urgent imperative.
- Critical infrastructure has always been a primary target of threat actors and different governments, for many reasons, including its impact on a nation's economy and resources and for financial gain.
- Many critical infrastructure sectors rely on control systems such as Supervisory Control and Data Acquisition (SCADA) and Programmable Logic Controllers (PLC) to control and monitor devices. However, these systems introduce new cybersecurity vulnerabilities that must be monitored and secured.
The Role of Nation-State Actors
Geopolitical tensions have spilled into the digital realm. Nation-state actors are increasingly playing a role in sophisticated cyber campaigns. These actors are often driven by political motives. They use advanced techniques to compromise sensitive data and disrupt operations. This is to advance their strategic interests in the global cyber landscape.
The Need for a Paradigm Shift in Cybersecurity
The recent surge in data breaches highlights the critical importance of reevaluating cybersecurity strategies. With cyber threats evolving and becoming more sophisticated, organizations must acknowledge that it’s not a matter of if they will be targeted, but rather when. To effectively combat these threats, proactive measures are essential.
Implementing robust cybersecurity frameworks is the foundation of a strong defense. This involves establishing comprehensive policies, procedures, and technologies to protect against a wide range of cyber threats. A thorough framework encompasses elements such as network security, endpoint protection, access controls, encryption, and incident response protocols.
Continuous monitoring is another crucial component of proactive cybersecurity. By continuously monitoring networks, systems, and applications for suspicious activities or anomalies, organizations can detect potential threats early and respond swiftly to mitigate damage. This proactive approach helps prevent breaches from escalating into full-blown cyber incidents.
Equally important is fostering a culture of cyber awareness throughout the organization. Employees are often the first line of defense against cyber threats, but they can also be the weakest link if they’re not properly trained and educated. Promoting cyber awareness involves providing regular training sessions, conducting simulated phishing exercises, and encouraging employees to remain vigilant and report any security incidents promptly.
At Partek IT Solutions, we understand the urgency and complexity of modern cybersecurity challenges. Our team of experts specializes in designing and implementing tailored cybersecurity solutions to address the specific needs and risks faced by your organization. Whether you’re looking to enhance your existing cybersecurity measures, implement new technologies, or train your staff — we’re here to help.
Don’t wait until it’s too late—take proactive steps today to safeguard your organization’s sensitive data and reputation. Contact us now to learn more about how we can help strengthen your cybersecurity posture and protect your business from cyber threats.