Email threat types you need to know about.
Learn how inbox defense protects against increasingly sophisticated attacks:
A cyberattack can affect your business in many ways, depending on its nature, scope, and severity.
According to the FBI’s Internet Crime Complaint Center (IC3), cybercrime cost $3.5 billion in losses in 2019 alone, with business email compromise causing the most damage. That doesn’t include unreported losses.
The FBI’s Internet Crime Complaint Center received 467,361 complaints last year — more than 1,300 per day — with phishing responsible for 93 percent of email breaches.
There can be a variety of indirect and intangible costs from attacks, such as legal fees, regulatory fines, operational disruptions, a damaged brand reputation, and other severe consequences.
In today’s rapidly evolving environment, traditional email security solutions aren’t enough to protect businesses anymore.
You must also effectively defend against sophisticated email threats including spoofing, social engineering, and fraud.
While comprehensive email gateway defenses provide a solid foundation, using a multilayered protection strategy radically reduces susceptibility to email attacks and helps better defend your business, data, and people.
Let's take a look at the top email threat types, including their risks and impact on businesses, and how AI and API-based inbox defense can address the gaps in the email gateway and help provide total email protection against attacks.

Spam
Spam is unsolicited bulk email messages, also known as junk email.
Spammers typically send an email to millions of addresses, with the expectation that only a small number will respond or interact with the message. Spammers gather email addresses from a variety of sources, including using software to harvest them from address books. The collected email addresses are often also sold to other spammers. Some spam emails push scams, others are used to conduct email fraud. Spam also comes in the form of phishing emails that use brand impersonation to trick users into revealing personal information, such as login credentials and credit card details.
The Impact of Spam:
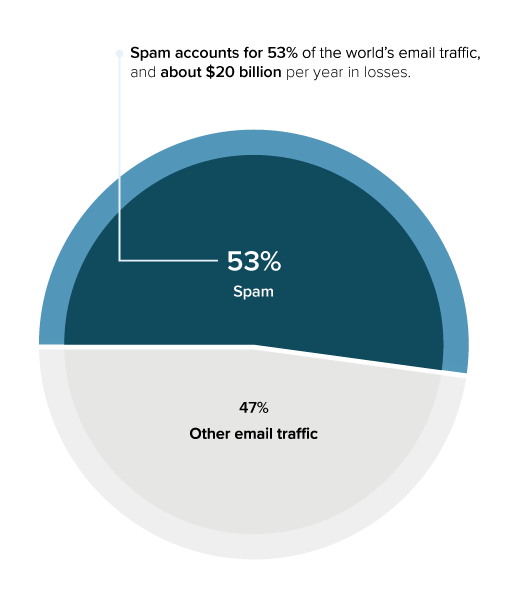
Spam costs businesses about $20 billion per year in losses. Spam mail lowers productivity by flooding inboxes with junk mail and impacts server traffic to process messages. In addition, it can be used to distribute malware and in large-scale phishing attacks.
Email defense against spam:
Modern gateways are very effective at blocking spam; inline deployment of spam filters helps stop spam before it hits the inbox. API-based inbox defense isn’t as effective against these large-scale attacks. Voluminous attacks, such as spam, can overwhelm email servers and have an adverse impact on inbox performance, creating a large inbox load before being clawed back by APIs.
Malware
Cybercriminals use email to deliver documents containing malicious software, also known as malware.
Typically, either the malware is hidden directly in the document itself, or an embedded script downloads it from an external website. Common types of malware include viruses, Trojans, spyware, worms, and ransomware.
Volumetric malware:
This type of malware is designed to be spread en masse and take advantage of older, unpatched systems using common vulnerabilities. It exploits known vulnerabilities and can generally be caught by signatures and simple heuristics. Volumetric malware is also know as: commodity malware and viruses.
Zero-day malware:
Advanced malware attacks use zero-day threats, which are ones that haven’t been seen before and don’t match any known malware signatures. They may exploit a previously unknown software vulnerability or use a new malware variant delivered by standard means. These zero-day attacks are impossible to detect with traditional signature-based solutions. Zero-day malware is also known as: 0Day.
URL attacks:
URLS that point to malicious websites or payloads are generally intended to trick users into clicking to download malware.
The Impact of Malware:
94% of malware is delivered via email. With ransomware, one of the most popular forms of malware, cybercriminals infect the network and lock email, data, and other critical files until a ransom is paid. These evolving and sophisticated attacks are damaging and costly. They can cripple day-to-day operations, cause chaos, and result in financial losses from downtime, ransom payments, recovery costs, and other unbudgeted and unanticipated expenses.
In 2019, ransomware costs may have hit $170 billion. This number includes not only ransoms paid out but losses in productivity, data, and other damages caused by the attack.
Email defense against malware
Malware protection is best done at the gateway level, before emails hit inboxes.
Signature matching remains an important tool to detect and block most malware variants. However, there are more advanced techniques available for detecting zero-day threats. Sandboxing is one such tool: suspicious files and links are analyzed in an isolated test environment to make sure they are safe before being delivered to users’ inboxes. New malware signatures can be created based on sandbox analysis, to help prevent future attacks.
Data Exfiltration
Data exfiltration is the unauthorized transfer of data from a computer or other device.
It can be conducted manually via physical access to a computer and as an automated process using malicious programming on the internet or a network. Attacks are typically targeted, with the objective of gaining access to a network or machine to locate and copy specific data. In addition to malicious attacks, data is frequently lost accidentally due to human error.
Impact of Data Exfiltration :
According to an annual IBM report, the average total cost of a data breach was $3.92 million in 2019. For some industries, such as healthcare, this number can almost double. Data breaches in the United States were the most expensive, with an average cost of $8.19 million. The average size of a data breach was 25,575 records. Data loss can lead to financial losses and have a long-lasting impact on an organization’s reputation.
Email defense against data exfiltration:
Secure email gateways are deployed in-line with mail flow; they filter both inbound and outbound messages. Data loss prevention (DLP) is a set of technologies and business policies to make sure end users do not send sensitive or confidential data outside the organization. A DLP system scans all outbound email to look for pre-determined patterns that might indicate sensitive data, including credit card numbers, Social Security numbers, and HIPAA medical terms. Messages containing this type of sensitive data are automatically encrypted.
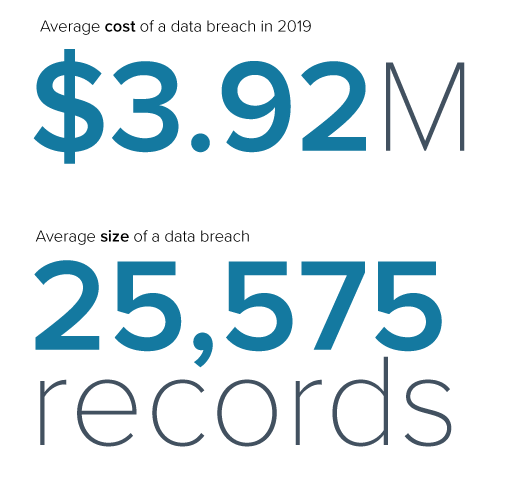
URL Phishing
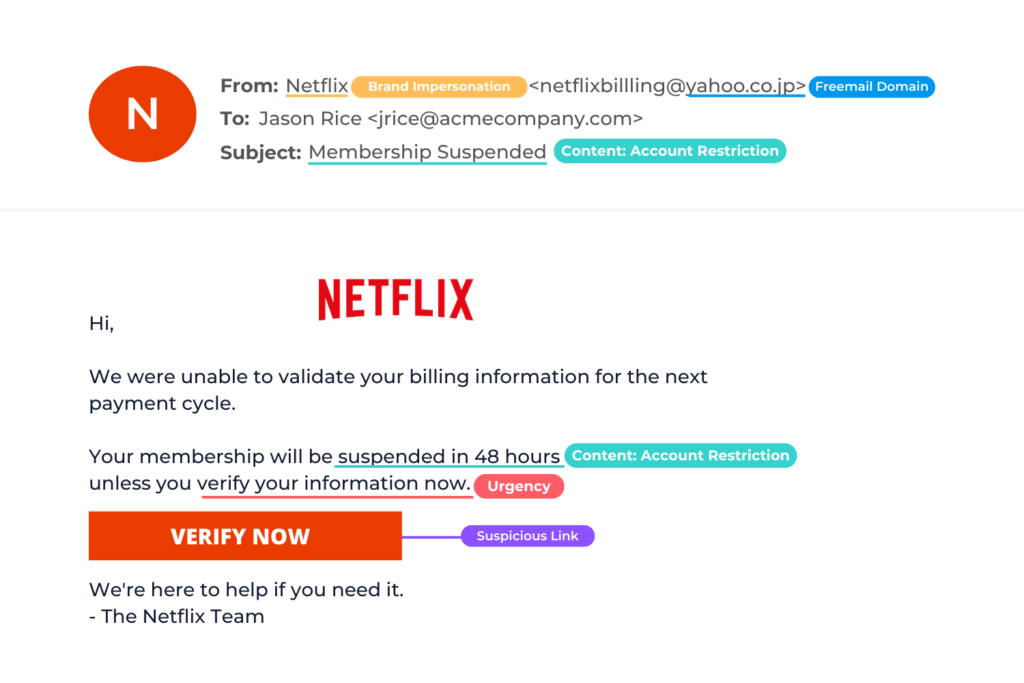
Cybercriminals use phishing attacks to try to obtain sensitive information for malicious use, such as usernames, passwords, or banking details.
With URL phishing, cybercriminals use email to direct their victims to enter sensitive information on a fake website that looks like a legitimate website.
Impact of URL phishing :
Around 32% of breaches involve phishing, and many phishing attacks include malicious links to fake websites. The use of URLs in phishing emails is popular and effective. Unfortunately, about 4% of recipients in any given phishing campaign click on a malicious link. Given the success rate, it’s not surprising that reported losses in 2019 due to phishing reached almost $58 million. That’s bad news, considering only 57% of organizations have URL protection in place.
Email defense against URL phishing:
Gateways are very effective at protecting against mass URL phishing attacks. Gateways deploy URL filtering and URL re-write technologies to block access to malicious website links distributed via email, including all known malware and phishing sites. Sandboxing can also help block malicious links. API-based inbox defense complements and completes the security a gateway provides. An API can enable a historical, internal view of actual URLs used by an organization. Abnormal or impersonating URLs, which signal phishing attacks, can be blocked. Even when a phishing website has never been used in previous campaigns or is hosted on a high-reputation domain, inbox defense can help protect against targeted spear-phishing attacks that use malicious URLs.
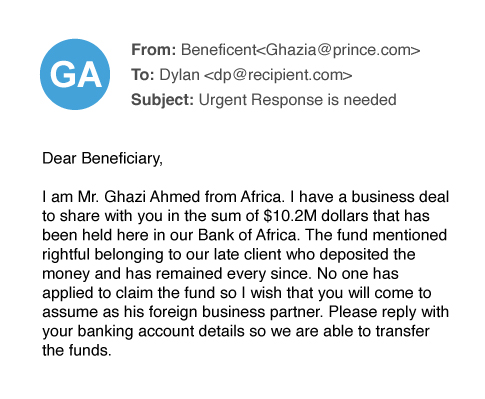
Scamming
In email scams, cybercriminals use fraudulent schemes to defraud victims or steal their identity by tricking them into disclosing personal information.
Examples of scamming include fake job postings, investment opportunities, inheritance notifications, lottery prizes, and fund transfers.
Impact of scamming:
Scamming accounts for 39% of all spear-phishing attacks. Scammers use a variety of different techniques, ranging from fake lottery wins to investment scams. It’s not unusual for scammers to try to monetize tragedies, such as hurricanes, the COVID-19 crisis, and other disasters. Scammers prey on an individual’s sympathy, charity, or fear. Unfortunately, many individuals fall for email scams, unwittingly sharing sensitive information or making payments to scammers.
Email defense against scamming:
API-based inbox defense against scamming uses historical email communications to determine what normal email communications look like for each employee. When criminals send scamming emails to their victims that fall outside of normal and expected communication, it’s flagged and blocked by inbox defense. Gateway solutions rely on granular policies, looking for specific keywords that indicate scams based on the content of the email. Combined with reputation filters and block lists, this can be effective, but it often leads to false positives, preventing important messages from being delivered to users’ inboxes. Organizations need to deploy both spam filters at the email gateway and API-based inbox defense for effective protection against scamming.
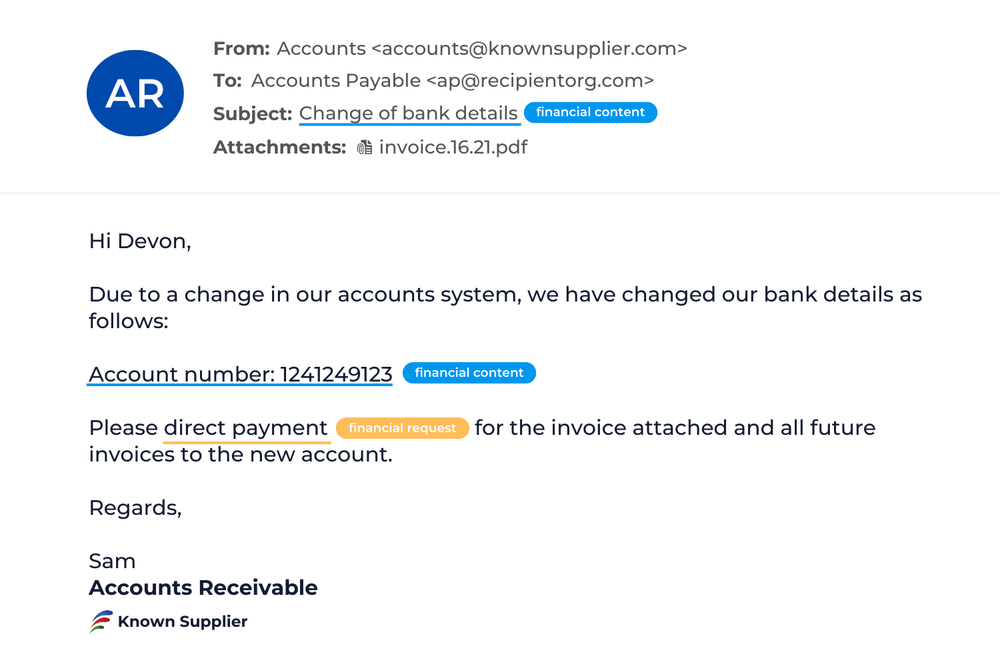
Spear Phishing
Spear phishing is a highly personalized form of email phishing attack.
Cybercriminals research their targets and craft carefully designed messages, often impersonating a trusted colleague, website, or business. Spear-phishing emails typically try to steal sensitive information, such as login credentials or financial details, which is then used to commit fraud, identity theft, and other crimes. Cybercriminals also take advantage of social-engineering tactics in their spear-phishing attacks, including urgency, brevity, and pressure, to increase the likelihood of success.
Impact of spear phishing:
43% of organizations claim they have been victims of a spear-phishing attack in the past 12 months, according to Barracuda’s recent Email Trends survey. However, only 23% of organizations said they have dedicated spear-phishing protection in place. When organizations fall victim to spear-phishing attacks, the impacts include malware infection of their machines and the network, direct monetary losses through wire transfers, and reputational damage. In many cases, spear-phishing attacks lead to the theft of credentials and email account takeover. Compromised accounts are often used to launch subsequent spear-phishing attacks. Organizations need dedicated spear phishing protection to stop this vicious cycle.
Email defense against spear phishing:
API-based inbox defense uses access to historical email communication data to build a communication identity graph, a statistical model that is specific to each user in the organization. This identity graph is then used to detect unusual communication patterns that fall outside of its statistical model, which in turn predicts and blocks spear-phishing attacks that make it past the gateway. Traditional email security gateways have no visibility into historical data. Therefore, they evaluate each email based on a set of predetermined policies, filters, and signatures, rather than on historical communication and context. Spear-phishing attacks are designed to bypass these filters and policies and therefore often delivered to users inboxes.

Domain Impersonation
Domain impersonation is often used by hackers as part of a conversation-hijacking attack.
Attackers attempt to impersonate a domain by using techniques such as typosquatting, replacing one or more letters in a legitimate email domain with a similar letter or adding a hard-tonotice letter to the legitimate email domain. In preparation for the attack, cybercriminals register or buy the impersonating domain.
Domain impersonation is a very high-impact attack. It can be easy to miss the subtle differences between the legitimate email domain and the impersonated email domain. For example, an attacker trying to impersonate partek.ca might use a very similar URL or change the top-level domain (TLD), using .net or .com instead of .ca, to fool victims.
Impact of domain impersonation:
In recent months, we have seen a sharp rise in domain-impersonation attacks used to facilitate conversation hijacking. Barracuda’s analysis of about 500,000 monthly email attacks shows a 400% increase in domain-impersonation attacks used for conversation hijacking.Email defense against domain impersonation:
The biggest challenge is accurate detection and differentiation an impersonation attempt from a real website. Email gateways must build lists of domains used by organizations and their partners over time, a long process that is prone to error and needs continuous management and updates. With so many email domains and variations, using gateways to detect domain impersonation leads to large numbers of false positives while also letting attacks through. An API-based inbox defense uses past email communications to get data on domains used by the organization, their partners, and customers. So, when a vendor sends an unusual request from the wrong domain, inbox defense detects and blocks it.

Brand Impersonation
Brand impersonation is designed to impersonate a company or a brand to trick their victims into responding and disclosing personal or otherwise sensitive information.
Service impersonation is a type of phishing attack designed to impersonate a well-known company or commonly used business application. The emails are well designed as an entry point to harvest credentials and carry out account takeover. Service impersonation attacks can be used to steal personally identifiable information, such as credit card and Social Security numbers.
Brand hijacking is a common form of phishing. It occurs when an attacker appears to use a company’s domain to impersonate a company or one of its employees. This is usually done by sending emails with false, or spoofed, domain names that appear to be legitimate. Brand hijacking is also known as: brand spoofing and domain spoofing
Impact of brand impersonation:
Service impersonation is used in 47% of all spear phishing attacks. Impersonating Microsoft is one of the most common techniques used by cybercriminals to take over an account. Microsoft and Office 365 credentials are high value because they allow hackers to penetrate organizations and launch additional attacks. Brand hijacking or spoofing attacks are made possible by a weakness in the email RFC standard that doesn’t require full authentication of sending domains. Standards like DKIM, SPF, and DMARC make it much more difficult to launch these attacks. However, domain spoofing is widely used by hackers in impersonation attacks. A recent study showed that there are almost 30,000 spoofing attacks each day. In addition, 77% of Fortune 500 companies do not have DMARC policies set up, making it easy for scammers to spoof their brands in phishing attacks.
Email defense against brand impersonation:
An API-based inbox defense against service impersonation uses past and internal email messages to get visibility into the services used by an organization. The data is used in a statistical detection model to understand the difference between fake and legitimate emails, including the branding and images of the legitimate services used by an organization. Gateways have no such visibility into the services used by an organization and can’t recognize the specific branding and images used by legitimate brands. They rely on predetermined policies, an approach that doesn’t scale given the variety of service impersonation attacks. API-based inbox defense is more effective at blocking service impersonation attacks. Organizations can get visibility into domain fraud using DMARC authentication to protect against domain spoofing and brand hijacking. DMARC reporting provides visibility into how an email domain is used, which in turn allows an organization to set up DMARC enforcement policies that will prevent spoofing of the domain.
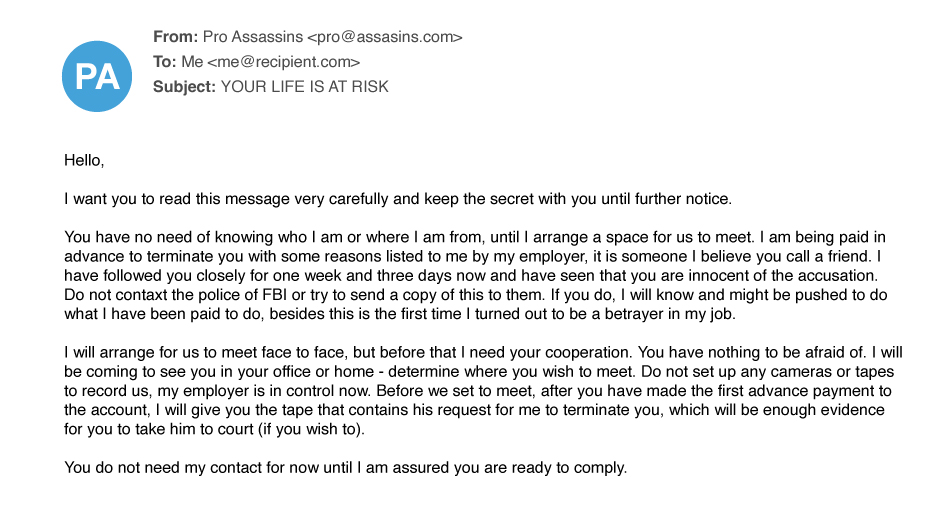
Extortion
Extortion scams, including sextortion, are increasing in frequency, becoming more sophisticated, and bypassing email gateways.
In sextortion attacks, cybercriminals leverage usernames and passwords stolen in data breaches, using the information to contact and try to trick victims into giving them money. The scammers claim to have a compromising video, allegedly recorded on the victim’s computer, and threaten to share it with all their contacts unless they pay up.
Impact of extortion:
Extortion makes up about 7% of spear-phishing attacks. According to the FBI, the cost of extortion attacks, was more than $107 million in 2019. On average, attackers ask for a few hundred or thousand dollars, an amount that an individual would likely be able to pay. Attackers rely on the large volume of attacks so that the small payments add up substantially. Extortion scams are under-reported due to the intentionally embarrassing and sensitive nature of the threats. IT teams are often unaware of these attacks because employees don’t report the emails, regardless of whether they pay the ransom.
Email defense against extortion:
Since inbox defense can access historical emails through APIs, it builds a statistical model of communication patterns, including the tone of voice used by individuals. This allows inbox defense to recognize the unusual and threatening tone of extortion attacks, in combination with other signals, to flag it as malicious email. While gateways can monitor for some signs of extortion, such as the use of certain keywords, a lack of visibility into historical email data and the inability to recognize an abnormal tone of voice prevents them from protecting organizations from extortion attacks.
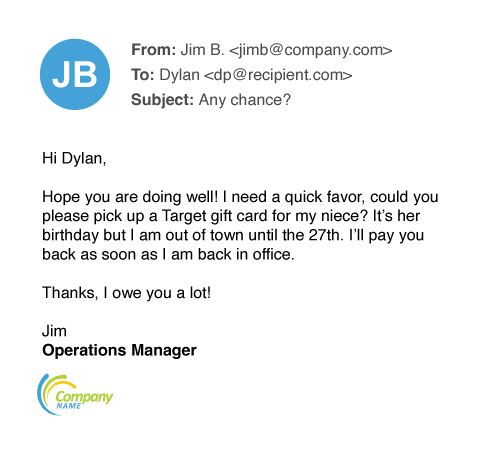
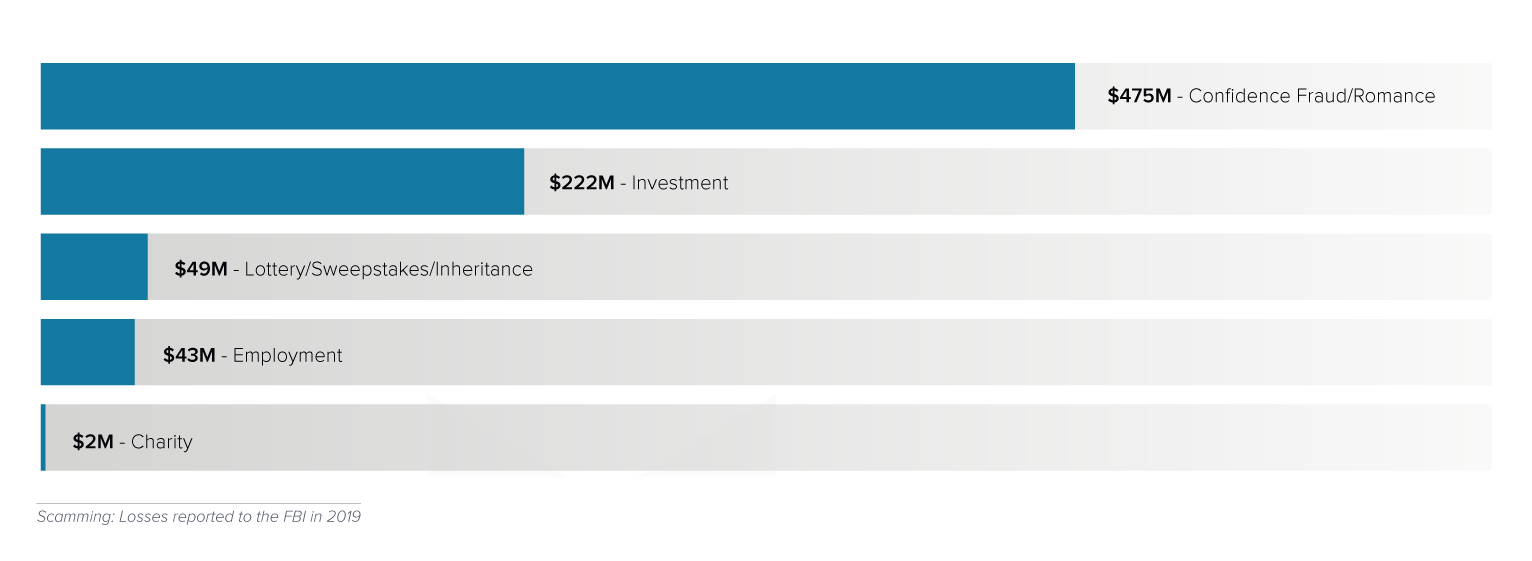
Business Email Compromise
In Business Email Compromise attacks, scammers impersonate an employee in the organization in order to defraud the company, its employees, customers, or partners.
In most cases, attackers focus their efforts on employees with access to the company’s finances or personal information, tricking individuals into performing wire transfers or disclosing sensitive information. These attacks use social-engineering tactics and compromised accounts, and they often include no attachments or links.
Impact of business email compromise:
While business email compromise makes up only 7% of spear-phishing attacks, according to the FBI, it caused more than $1.7 billion in losses in 2019. Gmail accounts are used to launch 47% of business email compromise attacks. Often these scams directly target human resources and payroll departments with the goal of getting an employee’s salary transferred to a different, fraudulent account. Hackers impersonate employees, providing new account details for the paycheck deposit. Payroll scams account for 8% of business email compromise attacks, but they are on the rise, growing more than 800% recently.
Email defense against business email compromise:
API-based inbox defense uses historical email data to build a statistical model or an identity graph to understand who is likely to communicate with each other and which names and identities they use. It also analyzes typical requests between employees within the organization using sentiment analysis. When an unusual request is made, API-based inbox defense identifies an impersonation attempt based on the history of communications, rather than the rules and policies relied on by traditional email gateways. Email gateways have no visibility into relationships and communication patterns between individuals based on historical data. Gateways rely on customized granular policies and DMARC for spoofing and impersonation protection. These techniques are not enough to protect against BEC, and their overreliance on predetermined policies leads to large numbers of false positives or negatives. API-based inbox defense is a more effective protection against BEC attacks.
Conversation Hijacking
With conversation hijacking, cybercriminals insert themselves into existing business conversations or initiate new conversations based on information they’ve gathered from compromised email accounts to steal money or personal information.
Conversation hijacking can be part of an account-takeover attack. Attackers spend time reading through emails and monitoring the compromised account to understand business operations and learn about deals in progress, payment procedures, and other details. Cybercriminals rarely use the compromised accounts to send a conversation hijacking attack, though. Instead, attackers use email-domain impersonation.
Impact of conversation hijacking:
In recent months, there’s been a sharp rise of more than 400% in domain-impersonation attacks used to facilitate conversation hijacking. While the volume of conversation hijacking in domain-impersonation attacks is extremely low compared to other types of phishing attacks, these sophisticated attacks are very personalized, making them effective, hard to detect, and costly.
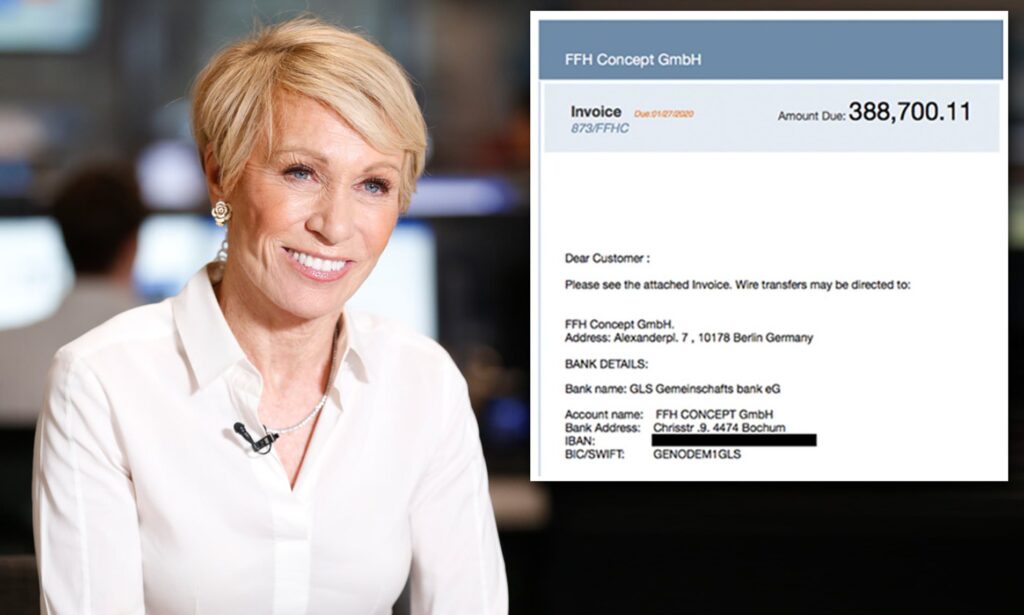
Barbara Corcoran, founder of real estate brokerage firm Corcoran Group and judge on ABC’s “Shark Tank,” was nearly scammed out of $400,000.
In one well-publicized case, the Shark Tank’s Barbara Corcoran lost nearly $400,000 due to a phishing scam. Scammers tricked her bookkeeper using email-domain impersonation, sending a bill that appeared to come from her assistant. But Corcoran’s assistant never sent the invoice; the fake bill came from an email that closely resembled her address. By the time Corcoran’s team realized something was wrong, the money had already been transferred to the scammers.
Email defense against conversation hijacking:
Inbox defense gains access to historical email communications through API integration, using that data in machine learning to understand who is likely to communicate with who, including usual external contacts and interactions with them. When an email conversation is hijacked and a trusted partner is impersonated by cybercriminals, inbox defense blocks the attack. Gateways have none of that visibility. While policies and allow lists can be created, this approach is difficult to scale and can lead to false positives. When a conversation is hijacked, the gateway delivers the email. Therefore, the gateway is unable to protect against this type of attack.
Lateral Phishing
With lateral phishing, attackers use recently hijacked accounts to send phishing emails to unsuspecting recipients, such as close contacts in the company and partners at external organizations, to spread the attack more broadly.
Because these attacks come from a legitimate email account and appear to be from a trusted colleague or partner, they tend to have a high success rate.
Impact of Lateral Phishing:
In a recent study, researchers found that 1 in 7 organizations has experienced a lateral phishing attack. These attacks, targeting a wide range of victims and organizations, can be extremely damaging to a business’s brand reputation, especially if they lead to additional widespread attacks in other organizations. More than 55% of these attacks target recipients with some work or personal connection to the hijacked account. Not surprisingly, about 11% of these attacks successfully manage to compromise additional accounts, leading to even more lateral phishing attacks.
Email defense against Lateral Phishing:
In most cases, lateral phishing is an internal attack. Email gateways have no visibility into these communications and can’t stop internal attacks because they never pass through it. Gateways can’t remediate attacks post-delivery, either. Once email is delivered to the inbox, it stays there. APIs for inbox defense provide visibility into internal communications. They can detect internal threats, such as lateral phishing, and remediate them post-delivery
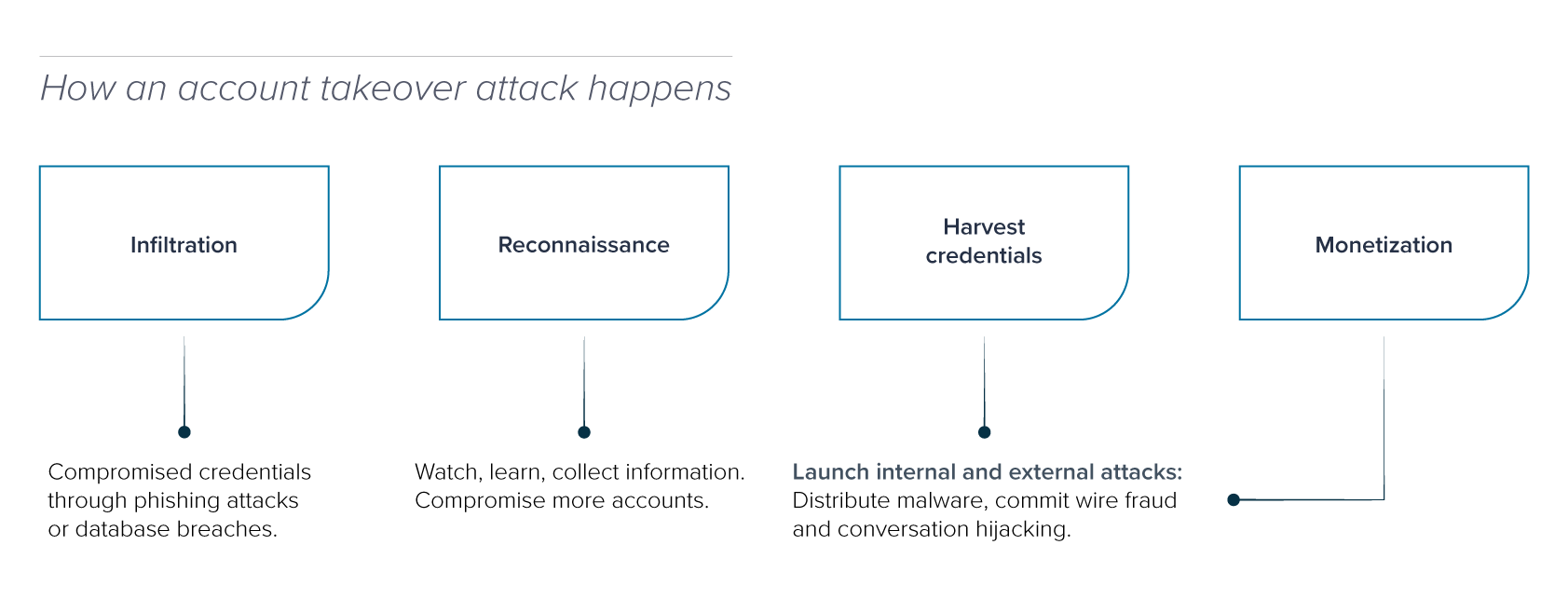
Account Takeover
Account takeover is a form of identity theft and fraud, where a malicious third party successfully gains access to a user’s account credentials.
Cybercriminals use brand impersonation, social engineering, and phishing to steal login credentials and access email accounts. Once the account is compromised, hackers monitor and track activity to learn how the company does business, the email signatures they use, and the way financial transactions are handled. This helps them launch successful attacks, including harvesting additional login credentials for other accounts.
Impact of Account Takeover:
Research has revealed a startling rise in account takeover, one of the fastest growing email security threats. A recent analysis of account-takeover attacks targeted at Barracuda customers found that 29% of organizations had their Office 365 accounts compromised by hackers in March 2019. More than 1.5 million malicious and spam emails were sent from the hacked Office 365 accounts in that one month!
Email defense against Account Takeover:
Gateways are positioned on the perimeter, outside of an organization, so they are disconnected from email inboxes and users. They lack the ability to monitor for suspicious behavior, such as logins from unusual locations or messages forwarded internally. An API-based inbox defense connects directly with users’ inboxes, monitoring for suspicious changes to inbox rules, unusual login activity, and malicious messages sent from already-compromised accounts. Inbox defense detects account takeover before it’s used to conduct fraud and remediates an attack by locking malicious users out of the compromised account.
How can you reduce susceptibility to targeted email attacks?
Email attacks have evolved to bypass traditional defenses and require organizations to set up protection, not only at the gateway, but also beyond it. Every business needs to deploy the right combination of technology and people to have effective email protection.
The threat landscape is continuously evolving, and organizations must adapt by investing in robust cybersecurity measures and fostering a culture of security awareness. By doing so, they can protect their assets, customer trust, and their very existence in an increasingly digital world.
Effectively protecting against evolving email threats:
Block high-volume attacks at the gateway and at the inbox level:
Gateways are the necessary foundation of email security. They block most malicious messages, including spam, large-scale phishing attacks, malware, viruses, and attacks from a perimeter defence perspective. Although gateways are important, they are no longer sufficient on their own. Deploying API-based inbox defense unlocks access to historical and internal email communication, which is necessary to protect your users against the highly targeted attacks that slip past gateways.
Educate users on the latest threats:
Some evolving and sophisticated phishing attacks, including those that use social-engineering tactics, can slip through the secure email gateway. Guard against these types of threats with security awareness training for employees. With continuous simulation and training, employees are able to recognize and report malicious content, transforming them into a layer of defense.
Scan your Office 365 environment
It’s fast, free, and safe with Partek's Email Threat Scanner.
Source: Barracuda




