Cyber Security Awareness Month: Multifactor Authentication
Staying safe online doesn’t have to be difficult.
But with people at the heart of cyber attacks, user knowledge and awareness are key.
To help you raise security awareness among your employees, Partek will be sharing a handful of free resources this month. Cyber attackers know that the people at your organization are your biggest security risk and are the easiest way to create a data breach within your business. We invite you to use and share these resources amongst your staff and workplace to help demonstrate how to better protect your organization from cyber threats.
This week’s focus will be on Multifactor Authentication (MFA):
The race to embrace MFA
When you add layers of authentication, you add layers of security to your accounts, data, and systems.
Authentication, in a security context, is about verifying your identity. You authenticate your identity on a regular basis; When you log into accounts and systems, the information you provide is intended to confirm your status as an authorized user. The problem with single-point authentication—think passwords and PINs—is that they are also a single point of failure. If a password is the only safeguard in place, and that password is compromised … well, then everything is compromised.
Multi-factor authentication (MFA)—also commonly referred to as two-factor authentication (2FA)—has gained steam over the past several years. Technology advancements have made it relatively simple to implement MFA for key accounts, data repositories, and cloud-based systems. But there is another driving force behind MFA adoption: Password theft and successful credential compromise attacks have skyrocketed.
What is MFA?
MFA enhances security by requiring two or more pieces of information—that is, multiple factors—during the authentication process.
There are three key factors in MFA:
- Something you know, like a password, PIN, or passphrase
- Something you have, like a real-time, unique verification code. These authentication codes are usually generated by a mobile app or security token, or they are delivered to you via a text message.
- Something you are, at a biometric level, like a fingerprint, iris scan, or voice pattern.
The 3 Factors of MFA
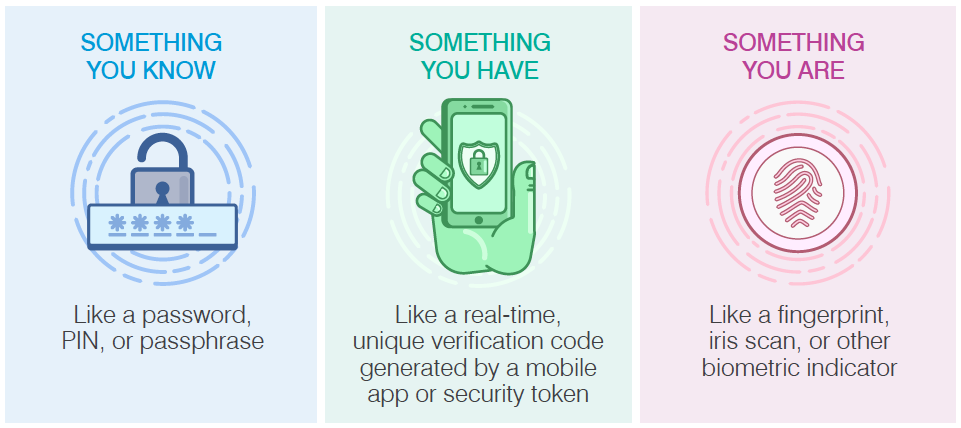
Source: Proofpoint
Always Opt for MFA
Organizations often require employees to provide multiple forms of authentication for assets like virtual private networks (VPNs) and cloud-based systems. Many websites and applications have also implemented MFA—but it is often left up to you to enable it. When it’s an option, always opt for MFA – it is well worth the few seconds it adds to your login process.
Here are three reasons you should always take advantage of MFA when it’s offered:
- It’s easy to add – Yes, you must take an action to enable MFA for your logins. But the process isn’t difficult. Sites and applications generally provide simple, step-by-step instructions and clearly explain when to expect an MFA prompt, and how to complete a login.
- It’s easy to use – As noted, there are multiple ways an organization might implement MFA. But regardless of the technology behind the additional authentication factor(s), MFA adds just a few seconds to your login process. (And the extra seconds are worth it.)
- It’s far more secure than a password alone – Cybercriminals have access to billions of stolen usernames and passwords on underground forums. So … what if the only thing standing between a criminal and your data, finances, and files is a compromised password? MFA helps to limit the damage that can be done if a threat actor steals (or buys) account credentials.



