Define your Cybersecurity Risk
Define your business's cyber security risk
It is widely acknowledged that people— not technology — are the most critical variable in today’s cyber threats.
Cyber attackers target people, exploit people, and ultimately, they are people. Assessing your user vulnerability is an essential part of good cyber defence – you need to know who in your organization is most likely to fall for a well-crafted piece of social engineering.
Social engineering works by exploiting human nature. Most people manage the volume of decisions they make in a day by using a mixture of habit, trial-and-error, and cognitive biases. As demands on our time and attention increase, so does our reliance on these routine habits. Cyber attackers recognize this, targeting users with demanding jobs, working in high-pressure departments. They know that these victims may not have the time to fully scrutinize a message before clicking a link or downloading an attachment.
In cyber security, risk is defined as:

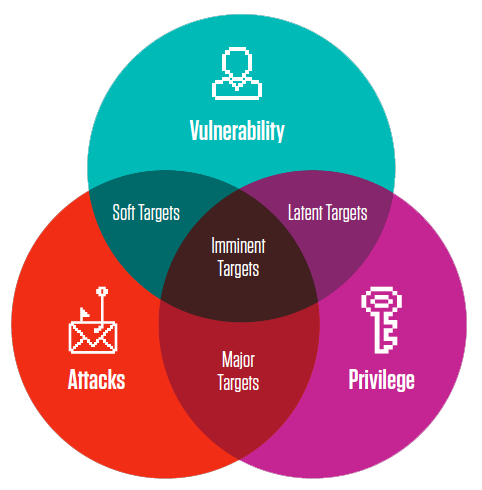
In other words, a people-centric risk model takes into account:
- Threats: The probability of someone being attacked
- Vulnerability: The likelihood that they will interact with a piece of malicious content sent to them
- Impact: How severe the impact could be if their credentials are compromised
To effectively prevent, detect, and respond to today’s threats and compliance risks, information security professionals must understand the people-centric dimensions of user risk: vulnerability, attack and privilege.
In practical terms, this means knowing:
- Where users are most vulnerable
- How attackers are targeting them
- The potential harm when privileged access to data, systems and other resources is compromised
Addressing those elements, the human factor of cybersecurity is the core pillar of modern defence against cyber attacks.
Each person is unique and so is their value to cyber attackers — and risk to employers.
Each staff member has distinct vulnerabilities, digital habits, and weak spots.
Staff can be exploited and attacked in a number of ways and with varying frequency. It is important to consider the different levels of access privileges to data, systems, and resources that each of your employees has. These intertwined factors determine a user’s overall risk.
Vulnerability
A users vulnerability starts with their digital behavior — how they work and what they click.
Many employees work remotely or access their company email through their personal devices. They may use cloud-based file storage and have third-party add-ons installed to their cloud apps. They may handle data in riskier ways than their coworkers or they may be particularly receptive to email phishing tactics.
Quantifying Vulnerability:
Most cyber attacks can’t succeed unless someone is fooled by them. Mitigating vulnerabilities starts with security awareness training and risk-based controls.
The easiest way to quantify vulnerability, without putting your organization at risk, is to test employee responses to simulated threats. Using phishing simulation tools is a great place to start and can provide valuable on your weakest links, with the added opportunity for consistent and engaging education.- Train users to spot and report malicious email. Regular training and simulated attacks can prevent attacks from becoming successful and help identify people who are particularly vulnerable. The best simulations mimic real-world attack techniques. Look for solutions that tie into current trends and the latest threat intelligence.
- Assume that users will eventually click some threats. Attackers will always find new ways to exploit human nature. Find a solution that neutralizes threats by applying additional layers of security to your most vulnerable users.
- Isolate risky websites and URLs. Keep risky web content out of your environment. Web isolation can be a critical safeguard against URL-based threats. The same technology can isolate users’ personal web browsing and web-based email services.
- Are your staff using their personal devices for work purposes?
- Are they accessing personal accounts on a employer-issued device?
- Are they allowing friends and family to use their work computers and phones?
Attacks
Not all cyber attacks are created equal — some are more dangerous, targeted, or sophisticated than others.
Attacks are the trigger point at which vulnerability and privilege are exposed. The more sophisticated or compelling the cyber attack, the more likely that even the most security-aware victim will fall prey to them. Attackers are always evolving and exposing defensive loopholes, so it is essential that automated defenses are dynamic enough to respond to novel threats. Security training should also be updated regularly with details from the latest campaigns
Quantifying Attacks:
Cyber attacks are inevitable, but with the right mindset, tools, and policies, they can be a manageable risk.
- Build a robust email fraud defense. Email fraud can be difficult to detect, so it is important to invest in a solution that can manage email based on custom quarantine and blocking policies. Your solution should analyze both external and internal email — attackers may use compromised accounts to fool users within the same organization.
- Protect cloud accounts from takeover and malicious apps.
- Partner with a qualified Information Technologist and Cyber Security Specialist. Targeted attacks call for advanced threat intelligence. Leverage a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets.
Privilege
Privilege, or the systems and data your users have access to, allows you to quantify exactly how much damage a breach could cause.
Privilege measures all the potentially valuable things people have access to — such as data, financial authority, key relationships, etc. Measuring this aspect of risk is crucial because it reflects the potential payoff for attackers and the harm to an organization, if compromised. The user’s position in the organizational chart is naturally a factor in scoring privilege, but it’s not the only factor. Naturally, high-privilege users are disproportionately targeted in attacks, however a valuable target can be anyone who allows an attacker to achieve their goal.
Also consider that privilege is also perhaps the area where organizations have the highest level of potential control.
Quantifying Privilege:
The goal of every cyber attacker is access to data, systems and other resources. The more privileged the victim, the more access attackers have—and the more damage they can do.
- Identify high risk departments that deal with sensitive information, such as finance, human resources and legal. Knowing where your highest privilege-based risks exist, whether that is individually or departmentally, is a crucial step in defending any organization from attack. High-privilege users dealing with sensitive or valuable data may benefit from additional layers of security or training.
- Deploy an insider threat management system to prevent, detect, and respond to malicious, negligent, and compromised users, particularly in remote or hybrid work settings.
- Respond quickly to potential privilege abuse with tools that can help you determine what happened before, during and after the incident and determine the user’s intent—without the usual false positives.
- Enforce security policies with user training, real-time reminders, and blocking when necessary
Today’s threats require a people-centric approach to prevention.
In the vast majority of cases, humananility matters more than the technical specifics of an attack. Cyber criminals are looking for relationships that can be leveraged, trust that can be abused, and access that can be exploited.
Deploy solutions that give you visibility into who’s being attacked, how they’re being attacked, and whether the attack was successful. Consider the individual risk each user represents, including how they’re targeted, what data they have access to, and whether they tend to fall prey to attacks.
Is your critical data protected from the latest threats?
Take Partek's Security Foundation Assessment to find out!
Source: Proofpoint




