What is a phishing email?
Do these Emails look Phishy?
Phishing (pronounced: fishing) is an attack that attempts to steal money or data by getting you to reveal personal information on websites or through emails that pretend to be legitimate. Often requesting credit card or banking information, passwords, or login credentials.
The following are some common examples of Phishing Emails:
Account Deactivation
Scenario: An email from PayPal arrives telling the victim that their account has been compromised and will be deactivated unless they confirm their credit card details. The link in the phishing email takes the victim to a fake PayPal website where they enter their credit card information in order to “reactivate” their account.
Only enter your log-in credentials through a company’s official app or domain by visiting them directly and avoid using links through email or text whenever possible. Better yet, use multifactor authentication, which requires two ways of identifying yourself when signing into an account, such as a password and a code sent to your cellphone.
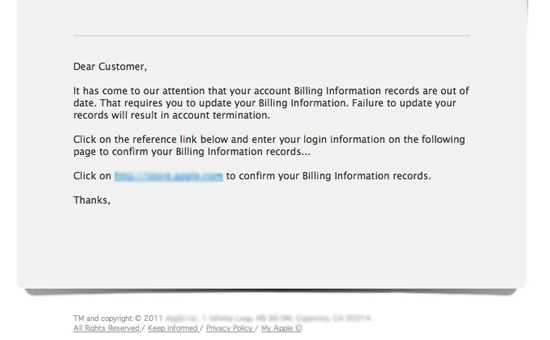
Source: Canadian Bankers Association
Transfer Funds
Scenario 1: You receive an email from your CEO about an urgent wire transfer that needs to be made. Thinking you’re helping out your boss, you comply and transfer the money.
Scenario 2: An urgent email arrives from a trusted friend who is currently travelling. The phishing email tells the victim that there is an emergency situation and requests a transfer of funds. The fund request is urgent and necessary to secure the persons safety. The victim doesn’t hesitate to transfer the funds, believing they are helping a trusted friend.
These emails look just like normal business communication and thus, raise no red flags. Scammers set up a legitimate-looking email address using information harvested from social networks. Through their online research, scammers are often able to use the appropriate first-names, real pictures or email signatures, or in some cases, research specifically who in the accounting department would be most likely to initiate a wire transfer.
Alternatively, some scammers are able to gain access to real staff email accounts through prior a phishing campaign.

Source: ACCC
Fake Invoice
Scenario 1: Your business’ accounting department receives an invoice from a well-known company for something you don’t recognize or remember purchasing. Sometimes these emails will include a fraudulent link to dispute or cancel the charges, but often they provide a phone number. Once in contact, they may request your personal information in order to “look up your account details” or they request a fee in order to get the charge reversed.
Scenario 2: We have run into instances where a vendor’s email was compromised and all of their incoming and outgoing emails are being monitored by the scammer. Often the scammer will filter specific emails into a hidden folder, so they are able to use the vendor’s email without the vendor suspecting that their account has been compromised. So, when a victim receives a request for payment of an invoice from the vendor’s account, the request is coming from the vendor’s legitimate email address for a legitimate invoice – so no red flags are raised. The scammer then uses the legitimate email address to request a change of banking information to receive the invoice payment to… and voila! The payment is sent to the new banking information and directly into the scammers account. The victim is then out the stolen money sent to the scammer in addition to the money still owed to the vendor.
It is best to take caution in any scenario where payment or banking details are discussed or requested through email. Avoid sharing banking details via email and contact the vendor directly over the phone to confirm the need to change the information. Taking a quick moment to confirm the invoice over the phone can protect you from engaging with fraudulent emails.
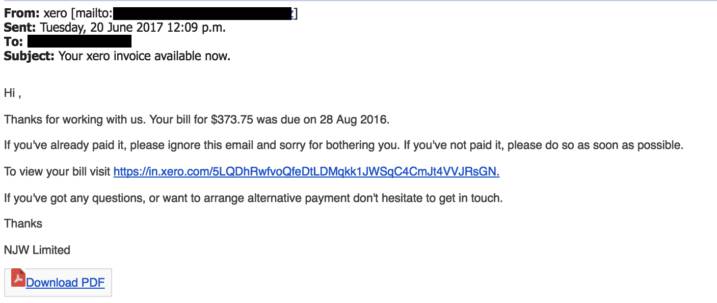
Source: Usecure
Unusual Activity
Scenario: An email arrives stating that there has been “suspicious activity on your account” or that “someone recently signed into your account” and alarm bells start ringing. The email then requests you to sign in to your account through a malicious link.
This scam is incredibly effective because victims aren’t just faced with urgency and panic – they’re also faced with confusion. The scammer’s goal when creating a sense of urgency is to force you into action so you avoid thinking rationally and critically. Keep your cool no matter how urgent an email appears to be, you always have time to give it a quick once-over and think about about the inconsistencies and legitimacy of the email request.

Source: Usecure
Expired Password
Scenario: An email arrives from Outlook stating that your password has expired and in order to maintain access to your account, you must immediately update your password. Victims are directed to a legitimate-looking login page where they can update their password. However, any credentials entered into this page will be sent straight to the cyber criminals.
Much like the previous example, the victim is often overwhelmed with a sense of panic or curiosity causing them to click links irrationally. Often the scammers goal is to trick recipients into opening a malicious link via a “Keep My Current Password” button in order to steal login credentials for email accounts. They then use the stolen email accounts to send more phishing emails, deliver malware, make monetary transactions, or sell the accounts on the darknet to other cyber criminals.
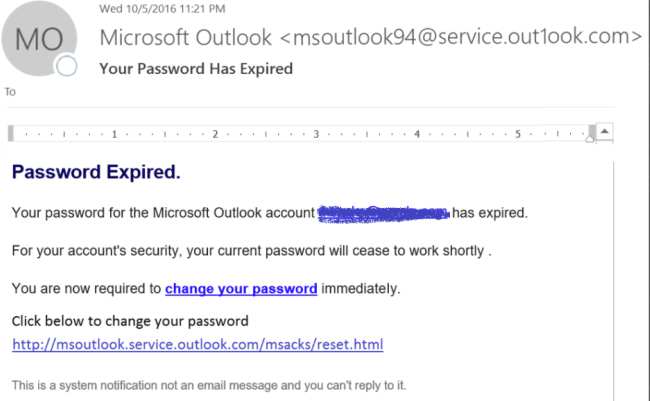
Source: Usecure
Download Document
An email arrives and requests you to click on the link in order to view a ‘document’. The link redirects you to a login page identical to a common cloud sharing platform – such as Google Docs or Dropbox. The victim then logs into their account in order to ‘grant access’ to the document and the attacker has free rein of their login credentials and account.
Sometimes the PDF attachments contain malware or exploit code, other times they may link to a convincing, but fraudulent, login page where you are asked to divulge sensitive information or login credentials. It is always important to verify any files you receive unexpectedly, even if they are from an entity that you recognize.
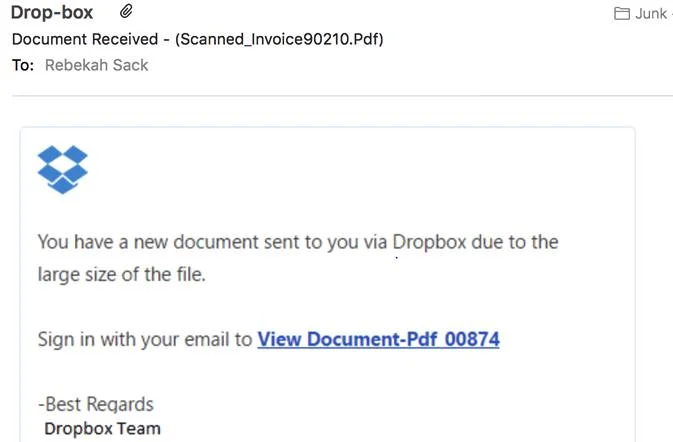
Source: Usecure




